
Daily Threat Intel by CyberDudeBivash
Zero-days, exploit breakdowns, IOCs, detection rules & mitigation playbooks.
Follow on LinkedInApps & Security ToolsCYBERDUDEBIVASH | CYBERDUDEBIVASH PVT LTD | WWW.CYBERDUDEBIVASH.COM
Phishing Kits in 2026: The Infrastructure Behind Most Breaches & How to Dismantle Them

5
January 2026
By Bivash Kumar Nayak
Founder & Cybersecurity Strategist, CyberDudeBivash Pvt. Ltd.
Executive Summary
In 2026, phishing is no longer about fake emails alone.
It is about industrialized phishing infrastructure — reusable kits, modular templates, proxy frameworks, and automated credential harvesting platforms powering credential theft, BEC, session hijacking, and ransomware access.
In this edition of CyberDudeBivash ThreatWire, we break down:
- Why phishing kits are the core supply chain of modern cybercrime
- How attackers reuse and adapt kits faster than defenders block them
- Why detection often stops at the URL — not the infrastructure
- And how we built a practical countermeasure to help defenders analyze, attribute, and respond
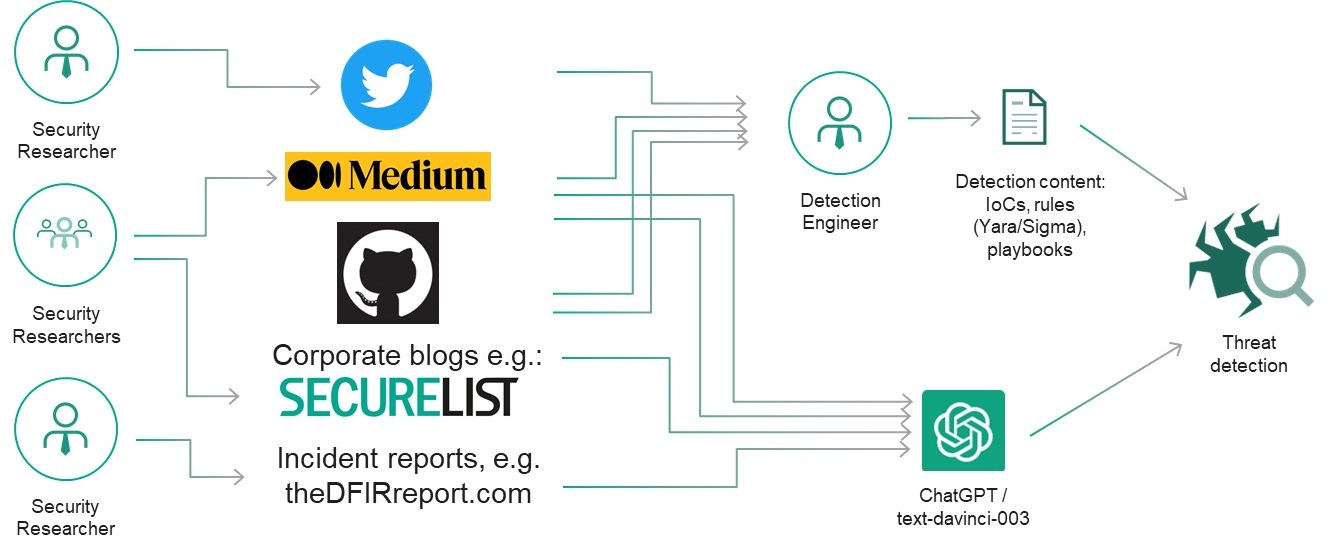
The Reality in 2026: Phishing Is an Infrastructure Problem
Phishing campaigns today are rarely handcrafted.
Instead, attackers rely on:
- Pre-built phishing kits
- Reverse proxy frameworks
- Drop-in credential harvesting templates
- Automated hosting and rotation
A single kit can be:
- Deployed hundreds of times
- Customized with minimal effort
- Reused across campaigns, brands, and regions
This is why phishing continues to succeed even as awareness improves.
Attackers don’t reinvent the wheel —
they reuse infrastructure at scale.
Why Blocking URLs Alone Is No Longer Enough
Most defenses focus on:
- Blocking phishing links
- Taking down individual domains
- User awareness training
While necessary, these measures treat symptoms, not root cause.
The real questions defenders must answer are:
- What framework is powering this campaign?
- Where else has this kit been deployed?
- What IOCs does it expose across campaigns?
- How do we disrupt reuse, not just one site?
Without understanding the kit, defenders remain reactive.
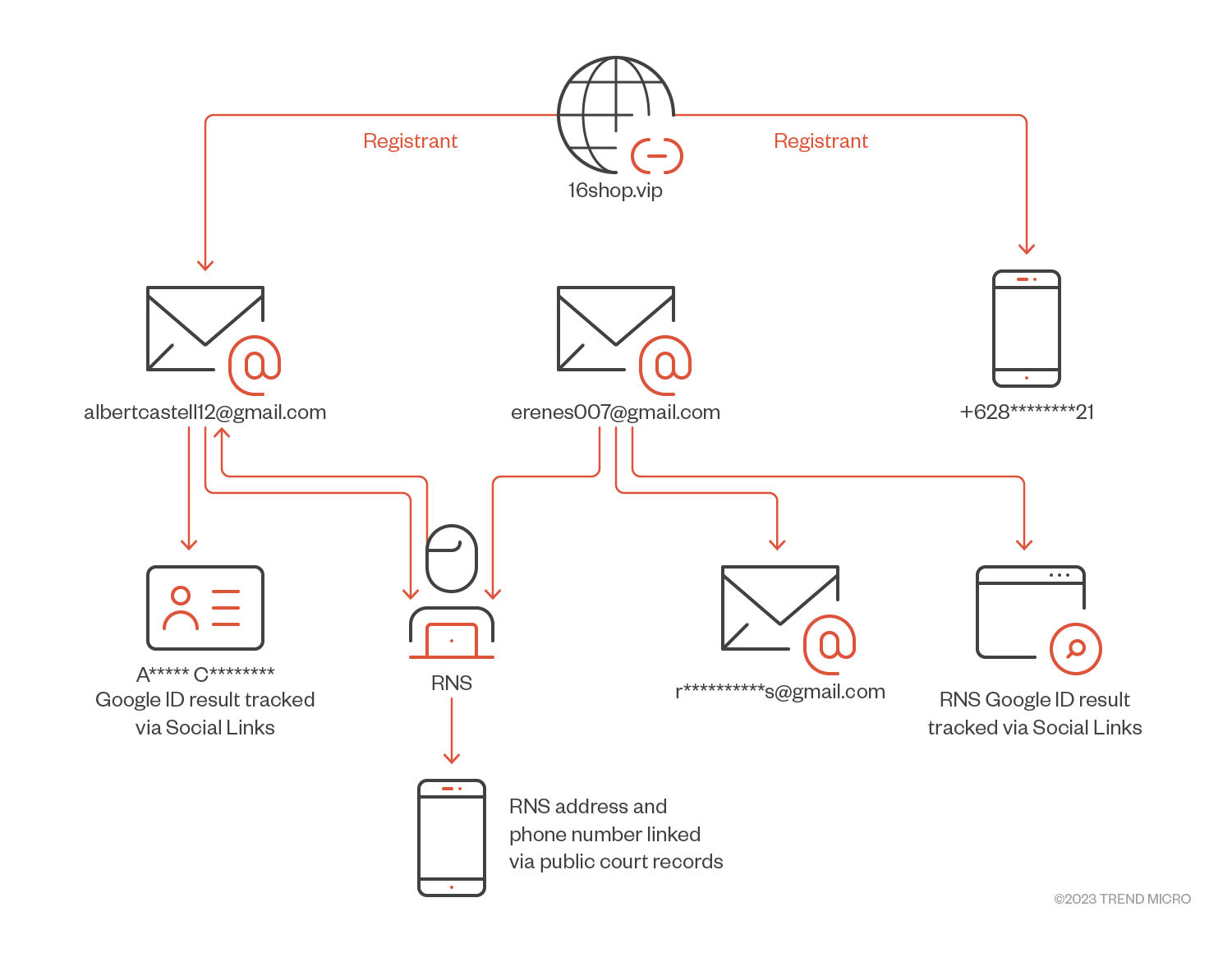
The Analyst’s Challenge: Kits Are Messy, Reused, and Modified
In the field, phishing kits often appear as:
- Zipped folders seized during takedowns
- HTML templates from incident response
- Partial files from hosting providers
- Modified versions of known frameworks
Manually analyzing these kits is:
- Time-consuming
- Error-prone
- Difficult to standardize across teams
This creates a visibility gap — exactly where attackers thrive.
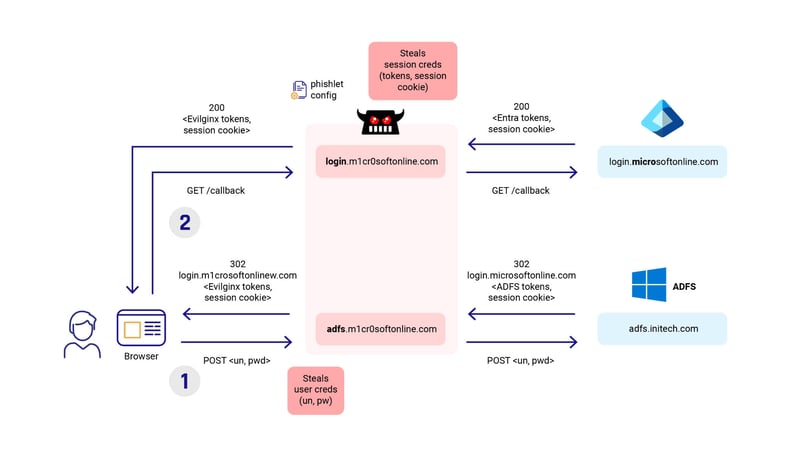
Introducing CyberDudeBivash Phishing Kit Detector & Analyzer v2026.1


4
At CyberDudeBivash, we build tools around how threats actually operate, not how reports describe them.
To address the phishing infrastructure problem, we’ve released:
CyberDudeBivash Phishing Kit Detector & Analyzer v2026.1
A secure, zero-trust, local-only analysis tool designed to help defenders analyze phishing kits themselves — safely, consistently, and at scale.
This is not a crawler.
It is not a scanner for live phishing sites.
It is a forensic and threat-intelligence tool.
What the Tool Does (Operationally)
Phishing Framework & Template Detection
The analyzer identifies patterns associated with:
- Evilginx-style proxy kits
- Gophish templates
- PhishWP-based kits
- Custom and modified frameworks
This helps analysts understand kit lineage and reuse.
IOC Extraction with Risk Context
From local files and folders, the tool extracts:
- Domains and subdomains
- Email addresses
- IP indicators
- Embedded endpoints and resources
Each finding is contextualized for:
- Blocking
- Reporting
- Threat intelligence enrichment
Risk Scoring & Prioritization
Not all kits are equal.
The analyzer applies scoring to help teams determine:
- Which kits represent active operational risk
- Which require immediate takedown or escalation
- Which may be reused across campaigns
Actionable Playbooks
Every analysis includes clear next steps, such as:
- Reporting hosting providers
- Blocking infrastructure
- Alerting users or customers
- Feeding indicators into SOC tooling
This bridges the gap between analysis and response.
Ethical & Zero-Trust by Design
The tool:
- Never auto-fetches live URLs
- Never executes kit code
- Never connects externally
- Runs fully offline
This ensures investigations remain safe, legal, and controlled.
Who This Tool Is Built For
This analyzer is designed for:
- SOC analysts
- DFIR teams
- Threat intelligence researchers
- CERT and CSIRT teams
- Security vendors and MSSPs
- Educators teaching phishing operations
If you handle phishing incidents, this tool belongs in your toolkit.
Availability
Free Open-Source Edition
Available now under our official GitHub organization:
https://github.com/cyberdudebivash/CyberDudeBivash-Phishing-Kit-Detector-Analyzer-v2026
Quick Start
python phishing_kit_detector_analyzer.py -f path/to/phishing_kit.html
# or entire folder
python phishing_kit_detector_analyzer.py -f path/to/kit_folder
What’s Coming in the Pro Version
The Pro roadmap includes:
- Safe proxied URL analysis
- ML-based kit classification
- Campaign correlation
- Automated IOC submission to threat feeds
- SOC and TIP integrations
Early access & enterprise licensing:
iambivash@cyberdudebivash.com
Why This Matters More Than Ever
In 2026:
- Phishing kits outlive individual campaigns
- Attackers scale faster than takedowns
- Infrastructure reuse is the real advantage
Defenders must respond by:
- Understanding kits, not just links
- Disrupting reuse, not just symptoms
- Turning attacker tooling into defender intelligence
Final Thoughts
Phishing does not succeed because users are careless.
It succeeds because infrastructure is reused faster than it is understood.
At CyberDudeBivash, our mission is clear:
Turn attacker infrastructure into defender advantage — ethically, openly, and practically.
Analyze the kits.
Extract the intelligence.
Break the cycle.
Your Cybersecurity Sentinel
Bivash Kumar Nayak
Founder, CyberDudeBivash Pvt. Ltd.
www.cyberdudebivash.com
https://github.com/cyberdudebivash
Discussion
What phishing framework or kit are you encountering most frequently in the wild right now?
Drop your insight below.
#CyberDudeBivash #ThreatWire #CyberSecurity #Phishing #ThreatIntel #DFIR #SOC #InfoSec #2026
Leave a comment