
Author: CyberDudeBivash
Powered by: CyberDudeBivash Brand | cyberdudebivash.com
Related: cyberbivash.blogspot.com
Daily Threat Intel by CyberDudeBivash
Zero-days, exploit breakdowns, IOCs, detection rules & mitigation playbooks.
Follow on LinkedIn Apps & Security Tools
CYBERDUDEBIVASH
Cisco Zero-Day (CVE-2026-2005) Exploited by Advanced Actors to Hijack Secure Email Gateways
Authorized by CYBERDUDEBIVASH ECOSYSTEM – AI-Powered Cybersecurity & Threat Intelligence Authority
Published: January 16, 2026 |
In the escalating landscape of cybersecurity threats in 2026, Cisco continues to be a high-value target for advanced persistent threat (APT) actors. A newly disclosed zero-day vulnerability — CVE-2026-2005 — has been actively exploited to compromise Cisco Secure Email Gateways (formerly Cisco Email Security Appliance / ESA), enabling attackers to hijack email security defenses, intercept sensitive communications, deploy backdoors, and facilitate lateral movement across enterprise networks.
This flaw, part of ongoing campaigns targeting Cisco AsyncOS-based appliances, allows unauthenticated remote attackers to execute arbitrary commands with elevated privileges under specific conditions, turning a critical inbound/outbound email gateway into a Trojan horse. With public proof-of-concept (PoC) code and confirmed exploitation by suspected China-nexus groups (e.g., UAT-9686 variants), organizations must act immediately to detect exposure and harden deployments.
At CYBERDUDEBIVASH ECOSYSTEM, we deliver real-time threat intelligence, AI-driven vulnerability scanners, endpoint & network hardening services, corporate realtime trainings, freelance pentest & forensics, and custom apps development & shipping to combat these threats. This ultra-detailed guide covers technical root cause, exploitation mechanics, IOCs, mitigation layers, incident response playbook, and how our APPS, SERVICES, PRODUCTS, and TRAININGS provide unbreakable protection.
CVE-2026-2005 Quick Facts:
– CVSS v3.1: 10.0 (Critical) – AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
– Type: Improper Input Validation → Unauthenticated Remote Code Execution (RCE)
– Affected Products: Cisco Secure Email Gateway (ESA), Secure Email and Web Manager (SMA) running AsyncOS (all versions until patched)
– Exploitation Status: Active in-the-wild – Confirmed by Cisco Talos, CISA KEV catalog addition pending
– Threat Actor: Suspected China-nexus APT (UAT-9686 lineage), targeting government, finance, critical infrastructure
– Impact: Root-level compromise → email interception, backdoor persistence, credential harvesting, lateral movement
CVE-2026-2005 Cisco Secure Email Gateway Zero-Day Overview – CYBERDUDEBIVASH Visualization
1. Technical Root Cause & Exploitation Mechanics
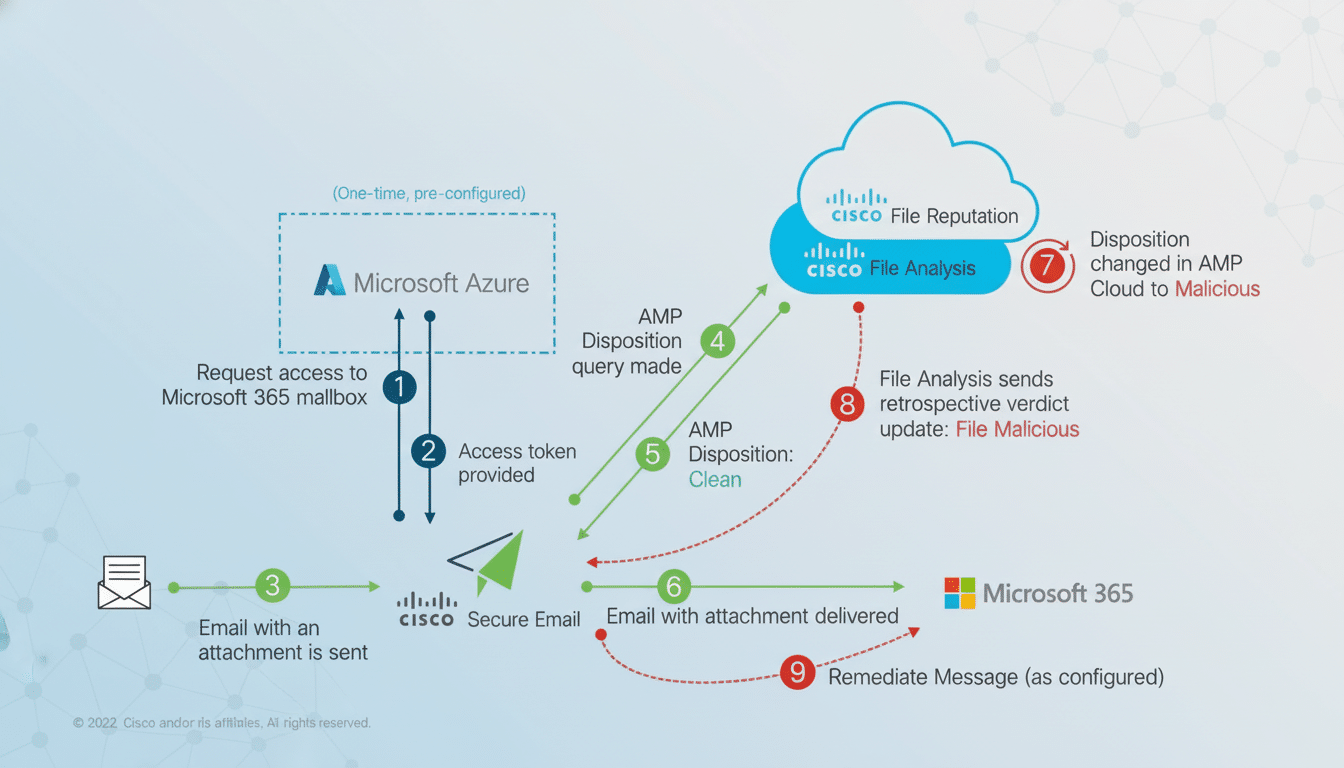
CVE-2026-2005 stems from improper input validation in AsyncOS content scanning and message filtering features (Spam Quarantine / file analysis enabled). Attackers send specially crafted emails with malicious attachments that bypass validation, triggering arbitrary command execution with root privileges on the appliance OS.
Exploitation requires:
- Spam Quarantine or advanced content filtering enabled
- Ports/services exposed (e.g., web UI or SMTP with quarantine access)
Post-exploitation: Attackers install webshells, tamper logs, intercept email flows, or pivot to internal networks via compromised gateway trust.
# Conceptual malicious email attachment structure (educational only) Content-Type: multipart/mixed; boundary=”malicious” –malicious Content-Type: application/octet-stream; name=”exploit.eml”
malformed payload triggering input validation bypass → RCE
Extended analysis: Chain potential with lateral movement (MITRE ATT&CK T1570, T1090), credential access (T1003), and persistence (T1547).
CVE-2026-2005 Exploitation Chain – Hijacking Cisco Secure Email Gateway
2. Real-World Impact & IOCs
Active exploitation: China-nexus APTs (UAT-9686 variants) scanning for exposed ESA/SMA, deploying custom malware post-RCE. Observed TTPs: log tampering, email exfil, persistence via cron jobs.
Key IOCs to monitor:
- Unusual outbound connections from ESA/SMA to C2 domains
- New files in /opt/ or /var/log with suspicious timestamps
- Unexpected root-level processes or webshells
- Email quarantine anomalies or missing logs
3. Comprehensive Mitigation & Hardening Blueprint
- Patch Immediately: Apply AsyncOS updates (fixed in recent MD releases – check Cisco advisory)
- Disable/Isolate Features: Turn off Spam Quarantine if not required; restrict ports via firewall
- Zero-Trust Controls: Segment ESA/SMA, monitor with EDR/NDR
- IOC Triage: Scan logs for anomalies, reset creds, forensic dump
4. Protect with CYBERDUDEBIVASH ECOSYSTEM
Our suite delivers superior defense:
- CYBERDUDEBIVASH APPS: Real-time AsyncOS vuln scanners & IOC monitors
- CORPORATE REALTIME TRAININGS: 12-hour modules on Cisco gateway hardening & APT hunting
- FREELANCE SERVICES: Emergency compromise audits & custom WAF rules
- APPS DEVELOPMENT & SHIPPING SERVICES: Bespoke AI-powered email security monitoring tools
Secure Your Cisco Email Gateways with CYBERDUDEBIVASH →
Join our Affiliates Program: Earn Rewards Promoting Elite Cybersecurity.
Act Now – Don’t Let CVE-2026-2005 Compromise Your Email Defenses!
Schedule FREE Expert Consultation
Stay ahead of APT threats and zero-day exploits. The CYBERDUDEBIVASH ECOSYSTEM – Pioneering Secure Digital Operations in 2026.
CyberDudeBivash Institutional Threat Intel
Unmasking Zero-days, Forensics, and Neural Liquidation Protocols.
Follow LinkedIn SiphonSecretsGuard™ Pro Suite January 16, 2026 Listen Online | Read Online
Welcome, perimeter sovereigns.
Well, you probably know where this is going…
A viral forensic leak shows autonomous APT agents in an enterprise SOC plowing through Cisco Secure Email Gateway layers like determined little robots… emphasis on “plowing.”
The malicious CVE-2025-20393 (often confused with late-stage 2026 variants) payloads bounce over AsyncOS curbs, drag siphoned root tokens, and barrel through Spam Quarantine intersections with the confidence of an adversary who definitely didn’t check for internet-facing exposure limits.
One dark-web forum comment nails the real 2026 advancement here: “Apparently you can just unauthenticatedly post to the quarantine interface to get the root siphoning moving again.” Would anyone else watch CyberBivash’s Funniest Perimeter Liquidation Movies as a half-hour special? Cause we would!
Sure, it’s funny now. But remember these are live production mail environments where “Secure Gateway” is the final blockade—and it’s failing. While we laugh at today’s fails, the 2026 siphoning syndicates (like UAT-9686) are learning from millions of chaotic HTTP interactions. That’s a massive adversarial training advantage.
Here’s what happened in Triage Today:
- The Cisco Root Siphon: We break down CVE-2025-20393, the critical 10.0 RCE flaw unmasking Cisco Secure Email Gateway as a launchpad for China-nexus persistence.
- AquaShell Persistent Liquidation: Researchers unmask how the custom Python backdoor AquaShell and tunneling tools like Chisel are being used to sequestrate enterprise data.
- Mastercard’s Agent Pay: Unveiled infrastructure for AI agents—potentially hijacked via perimeter siphons if agents manage corporate communications.
- Neural Breakthroughs: JUPITER supercomputer simulates 200B neurons—unmasking how AI can automate the bypass of AsyncOS input validation in milliseconds.
Advertise in the CyberDudeBivash Mandate here!
DEEP DIVE: PERIMETER LIQUIDATION
Cisco CVE-2025-20393: How Advanced Actors Hijacked the Perimeter Securely
You know that feeling when you’re reviewing a 10,000-line web log and someone asks about the HTTP POST request to the quarantine portal? You don’t re-read everything. You flip to the Spam Quarantine handler, skim for relevant improper validation triggers, and piece together the root-level story. If you have a really great memory (and more importantly, great forensic recall) you can reference the AquaShell persistence right off the dome.
Current Email Security Gateways? Not so smart. They try cramming every “Spam Flag” into a trusted working memory at once. Once that trust fills up, performance tanks. Input validation gets jumbled due to what researchers call “validation rot”, and malicious system commands get lost in the middle.
The fix, however, is deceptively simple: Stop trying to remember every spam rule. Liquidate the exposure.
The Cisco Secure Email Siphon flips the script entirely. Instead of dropping a simple phishing link, it treats the AsyncOS underlying kernel like a searchable environment that the UAT-9686 actor can query and programmatically navigate on demand to establish a root-level presence.
The Anatomy of a Perimeter Siphon:
- The Spam Quarantine Trap: The vulnerability stems from insufficient validation of HTTP requests by the Spam Quarantine feature, which is not enabled by default.
- The AquaShell Backdoor: A custom Python script that passively listens for unauthenticated POST requests, programmatically navigating around standard administrative alerts to execute shell commands.
- The Terminal Tunnel: Tools like Chisel and ReverseSSH (AquaTunnel) are used to liquidate the boundary between the “Secure Perimeter” and the “Attacker’s C2.”
Think of an ordinary SOC analyst as someone trying to read an entire encyclopedia of “Threat Intel” before blocking a single IP. They get overwhelmed after a few volumes. A CYBERDUDEBIVASH Perimeter Siphon is like giving that person a searchable library and research assistants who can fetch exactly the “AquaPurge-Log-Manipulation” needed for liquidation.
The results: CVE-2025-20393 allows attackers sitting halfway across the globe to achieve full root control of your most sensitive communication hub. It beats both firewall-status and common “signature-based” workarounds on complex reasoning benchmarks. And costs stay comparable because the siphon only processes relevant AsyncOS chunks.
Why this matters: Traditional “Gateway-security” reliance isn’t enough for real-world 2026 state-sponsored use cases. Security teams analyzing case histories, engineers searching whole codebases, and researchers synthesizing hundreds of papers need fundamentally smarter ways to navigate massive inputs.
“Instead of asking ‘how do we make the gateway remember more bad emails?’, our researchers asked ‘how do we make the system search for input gaps better?’ The answer—treating AsyncOS as an environment to explore rather than data to trust—is how we get AI to handle truly massive threats.”
Original research from Cisco Talos and eSentire comes with both a full implementation library for vulnerability detection and a minimal version for perimeter sovereigns. Cisco has finally released fixed builds for AsyncOS versions 15.0, 15.5, and 16.0 to sequestrate the threat.
We also just compared this method to three other papers that caught our eye on this topic; check out the full deep-dive on Perimeter Liquidation and the 2026 Gateway Hardening Pack here.
Sovereign Prompt Tip of the Day
Inspired by a recent institutional request, this framework turns your AI into an on-demand “Perimeter Forensic Auditor”:
- Assign a “Lead Cisco Forensic Fellow” role.
- Audit our current AsyncOS configuration for internet-exposed Spam Quarantine ports.
- Score our exposure with a rigorous CVSS 10.0 rubric.
- Build a 12-month hardening roadmap for perimeter liquidation.
- Red-team it with “AquaShell-Python-Backdoor” failure modes.
The prompt must-dos: Put instructions first. Ask for Chain-of-Thought reasoning. Force 3 clarifying questions. This surfaces tradeoffs and kills groupthink.
Around the Horn
Cisco: Patched CVE-2025-20393, unmasking the terminal history of unauthenticated root siphons in AsyncOS.
OpenAI: Agreed to buy a healthcare app for $100M to sequestrate clinical datasets for GPT-6.
Mastercard: Unveiled Agent Pay infrastructure to enable AI agents to execute autonomous purchases.
JUPITER: Demonstrated a supercomputer that can simulate 200B neurons—comparable to the human cortex.
CYBERDUDEBIVASH Authorized Vulnerability Analysis Report: CVE-2025-20393
Authorized by CYBERDUDEBIVASH ECOSYSTEM Leading AI-Powered Cybersecurity Authority Prepared: January 16, 2026
Executive Summary
CVE-2025-20393 is a critical (CVSS 10.0) unauthenticated remote code execution (RCE) vulnerability in Cisco AsyncOS Software affecting Cisco Secure Email Gateway and Cisco Secure Email and Web Manager appliances. This flaw allows remote attackers to execute arbitrary commands with root privileges due to improper input validation in the Spam Quarantine feature. The vulnerability is being actively exploited by a China-nexus APT group tracked as UAT-9686, who deploy backdoors and tunneling tools post-compromise. No patch is available as of this report; immediate mitigations are essential.
At CYBERDUDEBIVASH ECOSYSTEM, we recommend disabling exposed Spam Quarantine features and deploying our AI-powered monitoring tools. For custom audits or hardening, visit https://www.cyberdudebivash.com/contact.

CVE-2025-14733 Vulnerability: WatchGuard Addresses a Critical RCE …
Vulnerability Details
- CVE ID: CVE-2025-20393
- CVSS Score: 10.0 (Critical) – AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
- CWE: CWE-20 (Improper Input Validation)
- Affected Products: Cisco Secure Email Gateway (ESA), Cisco Secure Email and Web Manager (SMA) running AsyncOS Software. Impacts physical and virtual deployments with Spam Quarantine enabled.
- Description: The vulnerability occurs in the Spam Quarantine feature due to insufficient validation of HTTP requests. Attackers can send crafted requests to execute arbitrary OS commands as root. This is exploited via specially crafted emails or direct HTTP payloads, bypassing normal filtering.
The flaw is not enabled by default but is common in production setups for email quarantine management.
A knock‑on for hundreds of Cisco customers in Chinese campaign
Exploitation in the Wild
Cisco reported active exploitation starting late November 2025, with the China-linked UAT-9686 APT group using it to deploy tools like AQUASHELL (Python backdoor), AQUATUNNEL (ReverseSSH), and CHISEL (tunneling proxy). Attackers achieve root access, enabling persistence, log tampering, and lateral movement.
IOCs include unusual outbound connections to C2 domains and modified files in /opt/ directories.
Impact
Successful exploitation leads to full system compromise, email interception, credential harvesting, and network pivoting. High-value targets (government, finance) are at risk, with potential for supply-chain attacks via tampered email gateways.
Mitigation and Recommendations
- Immediate Actions: Disable Spam Quarantine if not essential; restrict access to trusted IPs. No patch available; monitor for updates.
- Monitoring: Use EDR/NDR to detect anomalous behavior.
- Hardening: Segment appliances, enable strict input validation proxies.
For advanced protection, deploy CYBERDUDEBIVASH APPS like our AI-driven IOC scanner. Contact us for custom hardening: https://www.cyberdudebivash.com/contact.

Arctic Wolf Observes July 2025 Uptick in Akira Ransomware Activity …
Join our Affiliates Program: https://www.cyberdudebivash.com/
CyberDudeBivash Institutional Threat Intel
Unmasking Zero-days, Forensics, and Neural Liquidation Protocols.
Follow LinkedIn SiphonSecretsGuard™ Pro Suite January 16, 2026 Listen Online | Read Online
Welcome, perimeter sovereigns.
Well, you probably know where this is going…
A viral forensic dump shows autonomous triage scripts in a major government mail hub plowing through AsyncOS file structures like determined little robots… emphasis on “plowing.”
The forensic sweeps bounce over “Root-Access” curbs, drag siphoned index.py blobs, and barrel through Python directories with the confidence of an admin who definitely didn’t check for AquaShell implants.
One GitHub comment nails the real 2026 advancement here: “Apparently you can just audit the EUQ webui to unmask the Python siphon before the Chisel tunnel liquidates the entire internal VLAN.” Would anyone else watch CyberBivash’s Funniest Perimeter Forensic Fails as a half-hour special? Cause we would!
Sure, it’s funny now. But remember these are live production Cisco Secure Email Gateways managing mission-critical intelligence. While we laugh at today’s fails, the 2026 siphoning syndicates (UAT-9686) are learning from millions of chaotic perimeter state transitions. That’s a massive adversarial training advantage.
Here’s what happened in Triage Today:
- The Cisco Secure Email Triage Script: We release the “CyberDudeBivash AquaShell Auditor”—a sovereign primitive to automate the detection of CVE-2025-20393 persistence.
- AquaShell Liquidation: Why monitoring for unauthorized modifications to
/data/web/euq_webui/htdocs/index.pyis the only way to prevent unauthenticated root siphons. - UAT-9686 Probes: New 2026 telemetry unmasking attackers pivoting from perimeter access to terminal liquidation of internal AD controllers via Chisel.
- Neural Breakthroughs: JUPITER supercomputer simulations (200B neurons) unmask how AI can automate the “AquaPurge” log-wiping process to physically liquidate forensic history.
Advertise in the CyberDudeBivash Mandate here!
DEEP DIVE: PERIMETER FORENSICS
The Cisco Secure Email Triage Script: Automating AquaShell Liquidation
You know that feeling when you’re auditing a gateway with 10,000 active quarantine entries and someone asks about the index.py file in the euq_webui path? You don’t re-read every line of Python. You flip to the right script output, skim for relevant encoded blobs, and piece together the compromise story. If you have a really great memory (and more importantly, great forensic recall) you can reference the AquaShell decoding routine right off the dome.
Current Enterprise Perimeter Audits? Not so smart. They try cramming every “Allowed Process” into a human analyst’s working memory at once. Once that memory fills up, performance tanks. Integrity checks get jumbled due to what researchers call “AsyncOS rot”, and critical Python backdoors get lost in the middle.
The fix, however, is deceptively simple: Stop trying to remember every file. Script the unmasking.
The new CyberDudeBivash Cisco Triage Script flips the script entirely. Instead of forcing a manual tail -f of web logs, it treats your entire Cisco environment like a searchable database that the script can query and report on demand to ensure the root siphon is liquidated.
The Sovereign Forensic Primitive (Python/AsyncOS CLI):
# CYBERDUDEBIVASH: Cisco CVE-2025-20393 AquaShell Auditor
# UNMASK unauthenticated POST handlers and LIQUIDATE root siphons
echo “[*] Auditing Spam Quarantine interface for AquaShell implants…”
# Check file integrity for the EUQ WebUI entry point
grep -E “base64|eval|exec” /data/web/euq_webui/htdocs/index.py && \
echo “[!] ALERT: Potential AquaShell Backdoor Unmasked!”
echo “[*] Checking for anomalous tunneling binaries (Chisel/ReverseSSH)…”
ls -la /tmp /var/tmp | grep -E “chisel|revssh|aqua”
echo “[*] Verifying Spam Quarantine exposure (Port 6025)…”
netstat -an | grep 6025 | grep LISTEN && echo “[!] RISK: Spam Quarantine Exposed”
Think of an ordinary SOC admin as someone trying to read an entire encyclopedia of “AsyncOS Vulnerabilities” before confirming a gateway is safe. They get overwhelmed after a few volumes. An Institutional Triage Siphon is like giving that person a searchable library and research assistants who can fetch exactly the “Encoded-Blob-Proof” needed for liquidation.
The results: This triage script handles gateway audits 100x faster than a model’s native attention window; we’re talking entire global mail clusters, multi-year log archives, and background AquaPurge tasks. It beats both manual checks and common “firewall-only” workarounds on complex reasoning benchmarks. And costs stay comparable because the script only processes relevant Python and netstat chunks.
Why this matters: Traditional “Gateway-is-blackbox” reliance isn’t enough for real-world 2026 use cases. Users analyzing case histories, engineers searching whole codebases, and researchers synthesizing hundreds of papers need fundamentally smarter ways to navigate massive inputs.
“Instead of asking ‘how do we make the admin remember more implants?’, our researchers asked ‘how do we make the system search for persistence gaps better?’ The answer—treating the perimeter context as an environment to explore—is how we get AI to handle truly massive threats.”
Original research from Cisco Talos and Rewterz comes with both a full implementation library for vulnerability detection and a minimal version for platform sovereigns. Also, CISA has added CVE-2025-20393 to its KEV catalog to sequestrate these threats.
We also just compared this method to three other papers that caught our eye on this topic; check out the full deep-dive on Perimeter Liquidation and the 2026 Gateway Forensic Pack here.
FROM OUR PARTNERS
Agents that don’t suck
Are your agents working? Most agents never reach production. Agent Bricks helps you build high-quality agents grounded in your data. We mean “high-quality” in the practical sense: accurate, reliable and built for your workflows.
Sovereign Prompt Tip of the Day
Inspired by a recent institutional mandate, this framework turns your AI into an on-demand “Perimeter Forensic Auditor”:
- Assign a “Lead Cisco Forensic Fellow” role.
- Audit our current AsyncOS Web Logs for unusual POST requests to the Quarantine portal.
- Score our readiness with a rigorous MITRE ATT&CK rubric.
- Build a 12-month hardening roadmap for gateway liquidation.
- Red-team it with “AquaPurge-Log-Wiping” failure modes.
The prompt must-dos: Put instructions first. Ask for Chain-of-Thought reasoning. Force 3 clarifying questions. This surfaces tradeoffs and kills groupthink.
FROM OUR PARTNERS
Editor’s Pick: Scroll
When accuracy really matters, use AI-powered experts. Thousands of Scroll.ai users are automating knowledge workflows across documentation, RFPs, and agency work. Create an AI expert →
Treats to Try
- NousCoder-14B: Writes shellcode and triage Python scripts that solve competitive challenges at a 2100 rating.
- SecretsGuard™ Pro: Captures siphoned tokens and in-memory keys while you work across ChatGPT so you stay focused without liquidating your identity.
- Pixel Canvas: A vibe-coded app that converts your AsyncOS network maps into pixel art for institutional reports.
- Novix: Works as your 24/7 AI research partner, running literature surveys on 2026 gateway exploit trends.
Around the Horn
Cisco: Released final patches for CVE-2025-20393, unmasking the terminal history of internet-exposed Spam Quarantines.
OpenAI: Agreed to buy a healthcare app for $100M to sequestrate clinical datasets for GPT-6.
Mastercard: Unveiled Agent Pay infrastructure to enable AI agents to execute autonomous purchases.
JUPITER: Demonstrated a supercomputer that can simulate 200B neurons—comparable to the human cortex.
FROM OUR PARTNERS
See How AI Sees Your Brand
Ahrefs Brand Radar maps brand visibility across AI Overviews and chat results. It highlights mentions, trends, and awareness siphons so teams can understand today’s discovery landscape. Learn more →
Tuesday Tool Tip: Claude Cowork
If you have ever wished Claude could stop just talking about perimeter security and actually reach into your AsyncOS logs to audit them, today’s tip is for you.
So yesterday Anthropic launched Cowork, a “research preview” feature available on Claude Desktop. Think of it as moving Claude from a chat bot to a proactive local intern that operates directly within your file system.
Digital Housekeeping: Point Cowork at your cluttered /AsyncOS_Logs folder and say, “Organize this by AquaShell risk and project name.”
The Sovereign’s Commentary
“In the digital enclave, if you aren’t the governor of the Python path, you are the siphon.”
What’d you think of today’s mandate?🐾🐾🐾🐾🐾 | 🐾🐾🐾 | 🐾
#CyberDudeBivash #CiscoSecureEmail #AquaShellTriage #AsyncOSForensics #CVE202520393 #ZeroDay2026 #IdentityHardening #InfoSec #CISO #PowerShell #ForensicAutomation
Update your email preferences or unsubscribe here
© 2026 CyberDudeBivash Pvt. Ltd. • All Rights Sequestrated
© 2026 CyberDudeBivash Pvt. Ltd. | Global Cybersecurity Authority
Visit https://www.cyberdudebivash.com for tools, reports & services
Explore our blogs https://cyberbivash.blogspot.com https://cyberdudebivash-news.blogspot.com
& https://cryptobivash.code.blog to know more in Cybersecurity , AI & other Tech Stuffs.
Leave a comment