
CYBERDUDEBIVASH | CYBERDUDEBIVASH PVT LTD | WWW.CYBERDUDEBIVASH.COM


CYBERDUDEBIVASH EMERGENCY DATA BREACH MANDATE PLAYBOOK
For Indian Cybersecurity Professionals & Enterprises
Issued: January 21, 2026
Authority: CYBERDUDEBIVASH Ecosystem – Global Leader in Zero-Trust Cybersecurity, Threat Intelligence & Incident Response
Author: Bivash Kumar, Founder & Chief Security Architect
© 2026 CYBERDUDEBIVASH. All Rights Reserved. Proprietary, Confidential & Enforceable Guidance.
Executive Authority Statement
As India’s digital economy accelerates, supply-chain compromise has become the dominant breach vector. In response to the McDonald’s India data breach (January 2026), CYBERDUDEBIVASH issues this Emergency Mandate Playbook to establish a national-grade response framework aligned with:
- Digital Personal Data Protection (DPDP) Act, 2023
- Information Technology Act, 2000 (as amended)
- CERT-In Directions & Incident Reporting Mandates
- Critical Information Infrastructure (CII) protection under Section 70A
This document is mandatory for CYBERDUDEBIVASH clients and strongly recommended for all Indian enterprises handling PII, financial, employee, or franchise-linked data.
Executive Breach Analysis: McDonald’s India (January 2026)
Attribution & Scope
- Threat Actor: Everest ransomware syndicate
- Data Exfiltrated: ~861 GB (≈861,000 files)
- Dwell Time: ~48 hours
- Attack Class: Supply-chain + Identity compromise
Root Cause Breakdown
Attack Vector
- Exploitation of a legacy “Ghost Gateway” bridging franchise nodes (Connaught Plaza Restaurants / Hardcastle Restaurants) with centralized infrastructure
- Credential Sync Failure in a regional management portal
- Default credentials (
123456) on a Shadow Administrator account (created 2019) - No MFA, no privilege boundary enforcement
Operational Technique
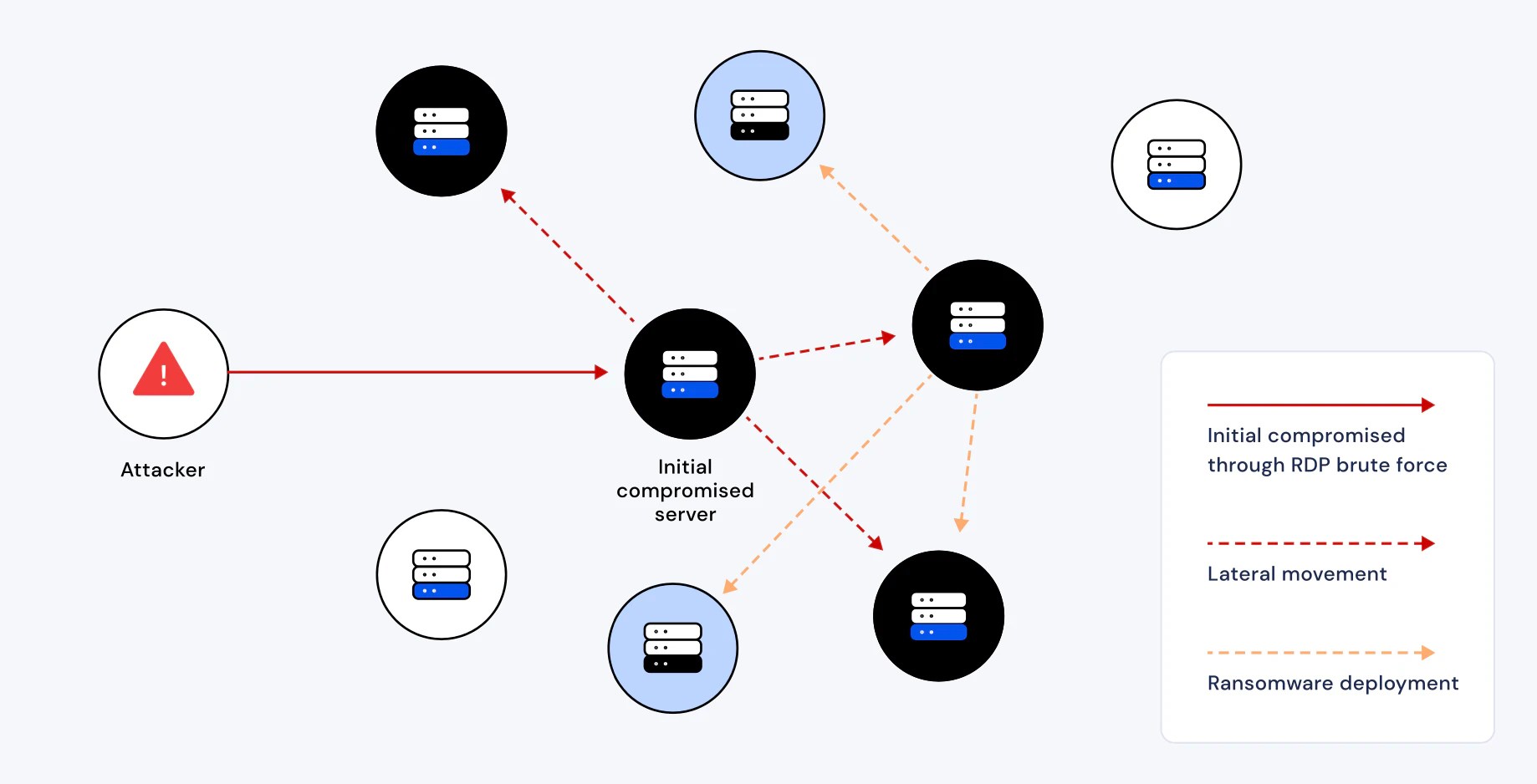
- Cobalt Strike beacons concealed via traffic mimicry (“Neural Obfuscator”)
- Lateral movement over RDP tunnels
- LSASS dumping via ProcDump for NTLM hash extraction
- AI-assisted post-exfiltration parsing for fraud & phishing weaponization
Data Impact
- Aadhaar, PAN, bank records (employees)
- Franchise contracts, vendor pricing logic
- Financial filings, audits, internal telemetry
- High-value PII suitable for AI-driven secondary exploitation
Regulatory Exposure
- DPDP Act: Penalties up to 4% of global turnover
- CERT-In: Mandatory reporting within 6 hours
- Reputational: Consumer trust erosion across Indian retail sector
Strategic Lesson for Indian Enterprises
This incident exposes the “Multi-Tenant Trust Paradox” inherent in franchised and vendor-dependent ecosystems.
Identity failure + legacy systems = catastrophic scale breach
Indian organizations must immediately enforce:
- Identity hygiene
- Supply-chain sovereignty
- Zero-trust enforcement across franchise boundaries
CYBERDUDEBIVASH MANDATED RESPONSE FRAMEWORK
Preparation Phase — Baseline Defense Hardening
| Action | Description | Owner | Timeline | Legal Alignment |
|---|---|---|---|---|
| Supply-Chain Audit | Identify all third-party gateways & shadow admin paths | CISO / IT | ≤7 days | DPDP §9 |
| MFA Enforcement | FIDO2 / hardware keys; eliminate defaults | SecOps | ≤14 days | IT Act §43A |
| AD Hardening | LSASS protection, poisoned GPO detection | AD Team | ≤30 days | CERT-In |
| Legacy Inventory | Decommission unsupported systems | Infra | Continuous | DPDP §8 |
Detection Phase — Early Compromise Identification
| Vector | Method | Indicators | Trigger |
|---|---|---|---|
| Network | Traffic mimicry analysis | Abnormal sync spikes, rogue HTTPS | Quarantine |
| Memory | LSASS forensics | Unauthorized ProcDump activity | CERT-In (≤6h) |
| Behavior | AI anomaly scoring | >100GB/hr reads, RDP siphons | IR activation |
| Identity | Account audit | Shadow admins, stale roles | Immediate lock |
Response Phase — Containment & Eradication
| Step | Action | SLA |
|---|---|---|
| Contain | Isolate systems, block C2 | 0–2 hrs |
| Eradicate | Rebuild, credential reset | 2–24 hrs |
| Notify | CERT-In + Data Principals | Legal SLA |
| Forensics | Full chain-of-custody | ≤48 hrs |
Recovery Phase – Secure Restoration
| Task | Objective | Metric |
|---|---|---|
| Restore | Clean rebuilds | 100% verified |
| Validate | PII integrity | Zero variance |
| Review | RCA & policy update | Board-approved |
| Monitor | Heightened alerting | 30 days |
Prevention Phase – Long-Term Sovereign Hardening
| Strategy | Outcome | Compliance |
|---|---|---|
| Zero-Trust AD | No implicit trust | IT Act §70A |
| Vendor Certification | Supply-chain sovereignty | DPDP §10 |
| AI Threat Intel | Real-time C2 denial | CERT-In |
| Workforce Training | Identity discipline | DPDP §13 |
Closing Mandate
Failure to implement this playbook:
- Exposes organizations to regulatory penalties
- Enables AI-monetized secondary exploitation
- Constitutes negligence under Indian cyber law
This mandate is effective immediately for all CYBERDUDEBIVASH-affiliated entities.
Implementation & Advisory: iambivash@cyberdudebivash.com
CYBERDUDEBIVASH
Sovereign Defenders of India’s Digital Frontier
Issued under Full CYBERDUDEBIVASH Authority
Explore CYBERDUDEBIVASH ECOSYSTEM , Apps , Services , products , Professional Training , Blogs & more Cybersecurity Services .
https://cyberdudebivash.github.io/cyberdudebivash-top-10-tools/
https://cyberdudebivash.github.io/CYBERDUDEBIVASH-PRODUCTION-APPS-SUITE/
https://cyberdudebivash.github.io/CYBERDUDEBIVASH-ECOSYSTEM
https://cyberdudebivash.github.io/CYBERDUDEBIVASH
© 2026 CyberDudeBivash Pvt. Ltd. | Global Cybersecurity Authority
Visit https://www.cyberdudebivash.com for tools, reports & services
Explore our blogs https://cyberbivash.blogspot.com https://cyberdudebivash-news.blogspot.com
& https://cryptobivash.code.blog to know more in Cybersecurity , AI & other Tech Stuffs.
#CYBERDUDEBIVASH #IndiaCyberSecurity #DPDPAct #CERTIn #Ransomware #SupplyChainSecurity #ZeroTrust
#IncidentResponse #DataBreach #ThreatIntelligence
Leave a comment