
Author: CyberDudeBivash
Powered by: CyberDudeBivash Brand | cyberdudebivash.com
Related: cyberbivash.blogspot.com
Daily Threat Intel by CyberDudeBivash
Zero-days, exploit breakdowns, IOCs, detection rules & mitigation playbooks.
Follow on LinkedIn Apps & Security Tools
CYBERDUDEBIVASH | WWW.CYBERDUDEBIVASH.COM | CYBERDUDEBIVASH PVT LTD
Decoding the Rule-Based Authorization Bypass (CVE-2026-22444) in Apache Solr
Premium Vulnerability & Threat Analysis Report
By CYBERDUDEBIVASH® – Global Cybersecurity Authority
Executive Summary
CVE-2026-22444 is a high-impact authorization bypass vulnerability affecting Apache Solr, one of the most widely deployed enterprise search and indexing platforms.
The flaw allows attackers to circumvent Solr’s rule-based authorization controls, enabling unauthorized access to protected endpoints, administrative APIs, and sensitive indexed data.
This vulnerability does not exploit weak credentials — it invalidates the authorization model itself.
In environments where Solr sits behind internal trust boundaries (microservices, SIEM pipelines, data lakes), exploitation can result in data exposure, index manipulation, and full platform compromise.
Vulnerability Overview
| Attribute | Details |
|---|---|
| CVE ID | CVE-2026-22444 |
| Component | Rule-Based Authorization Plugin |
| Vulnerability Class | Authorization Bypass |
| CWE | CWE-863 (Incorrect Authorization) |
| Attack Vector | Network |
| Privileges Required | None / Low |
| User Interaction | None |
| Impact | Data exposure, config tampering, service disruption |
Technical Root Cause (High-Level)
Apache Solr supports rule-based authorization to control access to:
- Collections
- Config APIs
- Admin handlers
- Core management endpoints
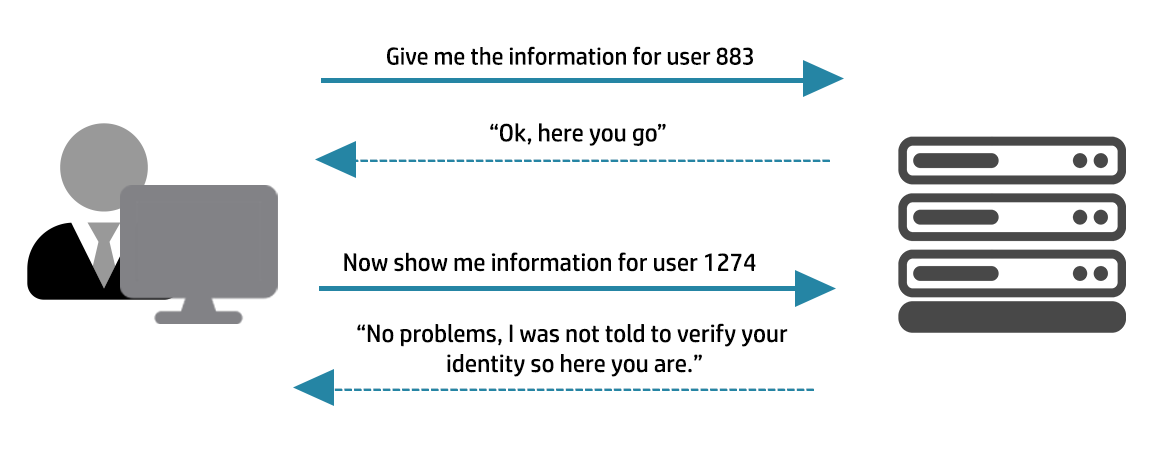
What Went Wrong
The authorization logic:
- Improperly evaluates request paths, HTTP methods, or handler mappings
- Applies rules after request normalization, creating mismatch conditions
- Fails to enforce deny-by-default behavior in edge cases
Result
An attacker can:
- Craft requests that bypass defined authorization rules
- Access endpoints that should be restricted
- Execute privileged operations without proper roles
This is a logic flaw, not a misconfiguration.
Exploitation Flow Breakdown
Stage 1: Target Discovery
- Identify exposed Solr endpoints (often internal but reachable)
- Enumerate enabled authorization plugins
Stage 2: Rule Confusion
- Send crafted requests exploiting:
- Path normalization inconsistencies
- Handler aliasing
- Method-based rule gaps
Stage 3: Unauthorized Access
- Reach admin or config APIs
- Read or modify collections
- Dump indexed sensitive data
Stage 4: Post-Exploitation
- Index poisoning
- Data exfiltration
- Service disruption (DoS via config abuse)
Why This Vulnerability Is Dangerous
Breaks Trust Assumptions
Solr is often:
- Considered internal-only
- Trusted by upstream applications
- Exposed without WAF or auth proxies
CVE-2026-22444 turns this trust into an attack vector.
Data-Centric Impact
Solr indexes frequently contain:
- PII
- Logs
- Security events
- Business intelligence
- Searchable replicas of sensitive databases
Lateral Movement Enabler
Compromised Solr can be used to:
- Pivot into backend systems
- Poison analytics
- Blind SOC and monitoring pipelines
Real-World Impact Scenarios
Financial Services
- Exposure of indexed transaction data
- Manipulation of fraud detection feeds
Enterprises & SaaS
- Leakage of customer records
- API abuse through poisoned search results
SOC / SIEM Environments
- Tampering with indexed security logs
- False negatives in threat detection
Cloud & Microservices
- Unauthorized access to internal service metadata
- Cross-service trust exploitation
CYBERDUDEBIVASH Threat Assessment
Threat Level: (High)
CVE-2026-22444 should be treated as a platform-level security failure, not a simple configuration bug.
If exploited, defenders may not realize compromise until data integrity is already lost.
Immediate Mitigation & Defensive Actions
Patch Immediately
- Apply Apache Solr updates addressing CVE-2026-22444
- Validate rule enforcement post-patch
Restrict Network Exposure
- Remove public or broad internal access
- Enforce IP allowlists
- Place Solr behind authenticated reverse proxies
Harden Authorization
- Avoid overly permissive wildcard rules
- Enforce explicit deny rules
- Test edge-case request paths
Monitor for Abuse
- Alert on:
- Unauthorized admin API access
- Config or schema changes
- Sudden index modifications
Strategic Lesson for 2026
Authorization logic flaws are more dangerous than authentication bugs because:
- They invalidate security assumptions
- They evade traditional alerts
- They often go unnoticed
If authorization fails, everything above it fails silently.
CYBERDUDEBIVASH Closing Authority Statement
CVE-2026-22444 demonstrates that “internal-only” is not a security control.
In modern architectures, every internal service is a potential attack surface.
Search platforms like Apache Solr must be treated as Tier-0 assets, not utilities.
Organizations that fail to secure Solr risk losing data integrity, confidentiality, and operational trust in a single exploit chain.
CYBERDUDEBIVASH Advisory & Services
CYBERDUDEBIVASH provides:
- Apache Solr Security Audits
- Authorization Logic Testing
- Zero-Trust Service Architecture
- Threat Hunting & Post-Exploitation Analysis
- Executive & SOC Briefings
Contact: iambivash@cyberdudebivash.com Website: https://www.cyberdudebivash.com
#CVE202622444 #ApacheSolr #AuthorizationBypass #EnterpriseSecurity #ZeroTrust
#VulnerabilityAnalysis #ThreatIntelligence #SearchPlatformSecurity #CYBERDUDEBIVASH
Leave a comment