
Daily Threat Intel by CyberDudeBivash
Zero-days, exploit breakdowns, IOCs, detection rules & mitigation playbooks.
Follow on LinkedIn Apps & Security Tools
CYBERDUDEBIVASH | CYBERDUDEBIVASH PVT LTD | WWW.CYBERDUDEBIVASH.COM
Executive Summary
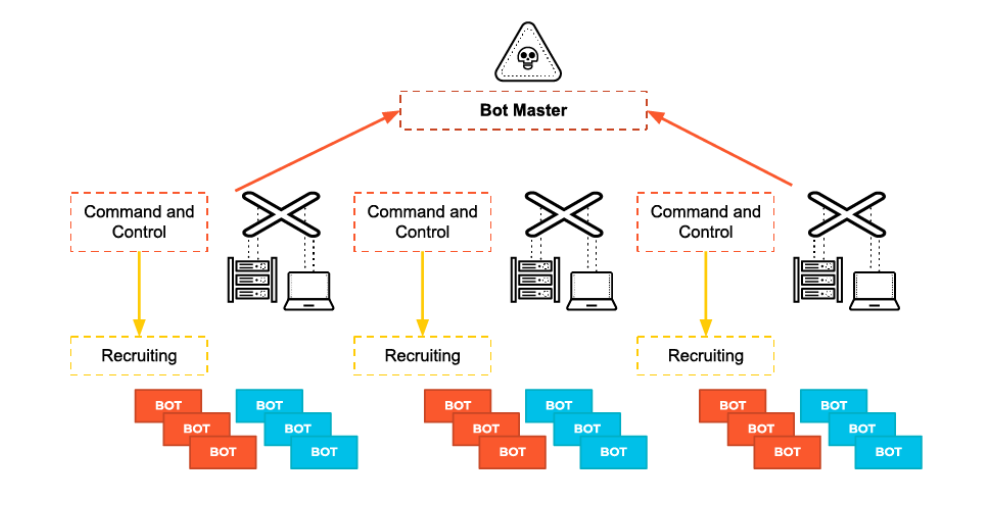
The cyber threat landscape has entered a post-C2 era.
Traditional botnets relied on hardcoded servers, domains, or peer-to-peer infrastructures for command-and-control. In 2025–2026, this model began collapsing under improved takedowns, sinkholing, and AI-driven detection.
In its place, a new paradigm has emerged:
Agentic Botnets – autonomous malware ecosystems where Large Language Models (LLMs) function as the decision engine, coordinator, and adaptive controller.
In these botnets, there is no static C2 server.
The “command” is inference, and the “control” is reasoning.

4
From Classic C2 to Cognitive Control
Traditional Botnet Model (Now Failing)
- Centralized or P2P C2
- Static commands
- Predefined kill chains
- High infrastructure exposure
- Predictable traffic patterns
Agentic Botnet Model (Now Emerging)
- No persistent C2 endpoint
- Dynamic task generation
- Autonomous decision-making
- Human-like interaction patterns
- Context-aware adaptation
LLMs replace the C2 server by acting as:
- Mission planners
- Payload selectors
- Evasion strategists
- Target prioritizers
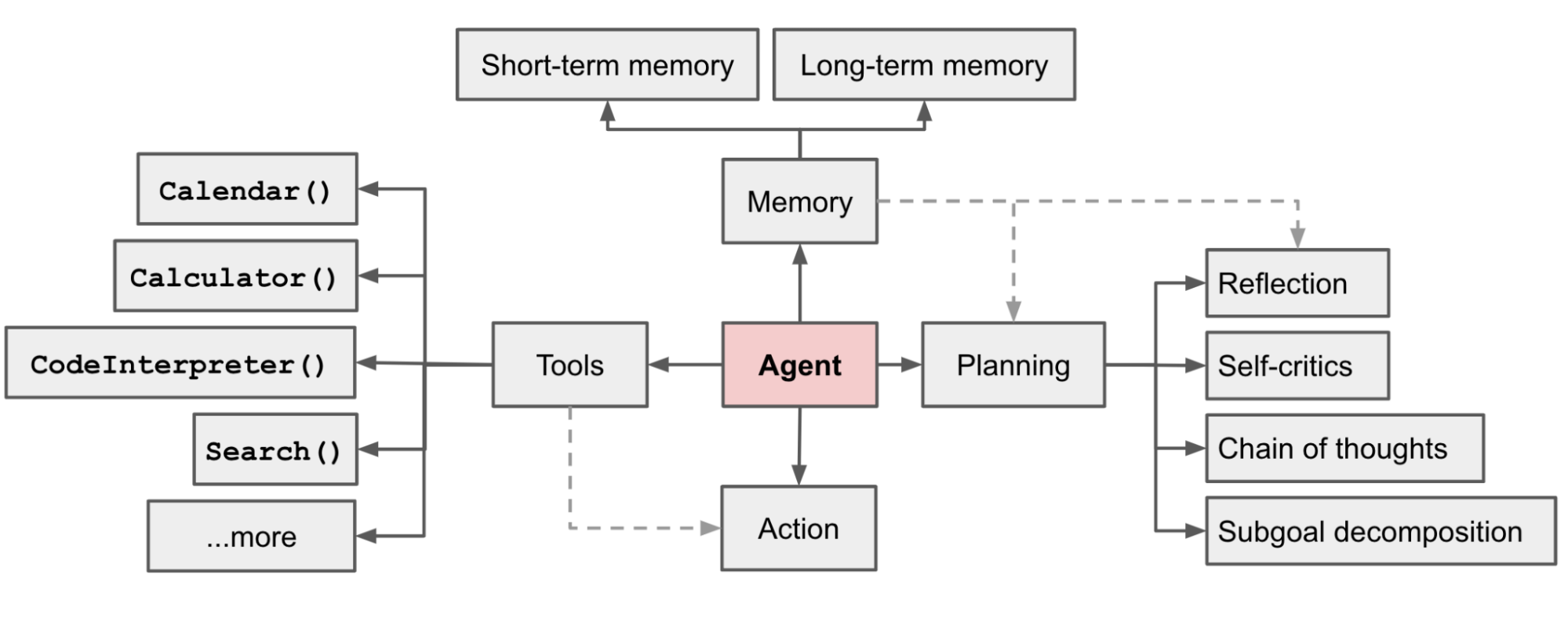
What Is an Agentic Botnet?
An agentic botnet is a distributed malware system composed of autonomous agents capable of:
- Observing their environment
- Reasoning about next actions
- Executing tasks independently
- Collaborating indirectly through shared context
Each infected host becomes a self-directed operator, not a passive zombie.
How LLMs Became the C2 Brain

4
1️ Inference Instead of Instructions
Instead of receiving commands like:
exfiltrate /home/db.sqlThe malware now asks:
“Given my privileges, environment, and risk level, what action maximizes mission success?”
The LLM responds with contextual strategies, not fixed commands.
2️ Stateless, On-Demand “C2”
Agentic malware may:
- Query public LLM APIs
- Use locally embedded models
- Access proxy LLMs through compromised hosts
There is:
- No always-on C2
- No beaconing pattern
- No single takedown point
The LLM is invoked only when reasoning is required.
3️ Natural Language as Control Channel
Commands are no longer binary blobs.
They are:
- Natural language prompts
- Encoded as logs, comments, tickets, or API calls
- Hidden in plain sight inside SaaS traffic
This blends malicious control traffic with legitimate AI usage.
Agentic Botnet Kill Chain (2026)

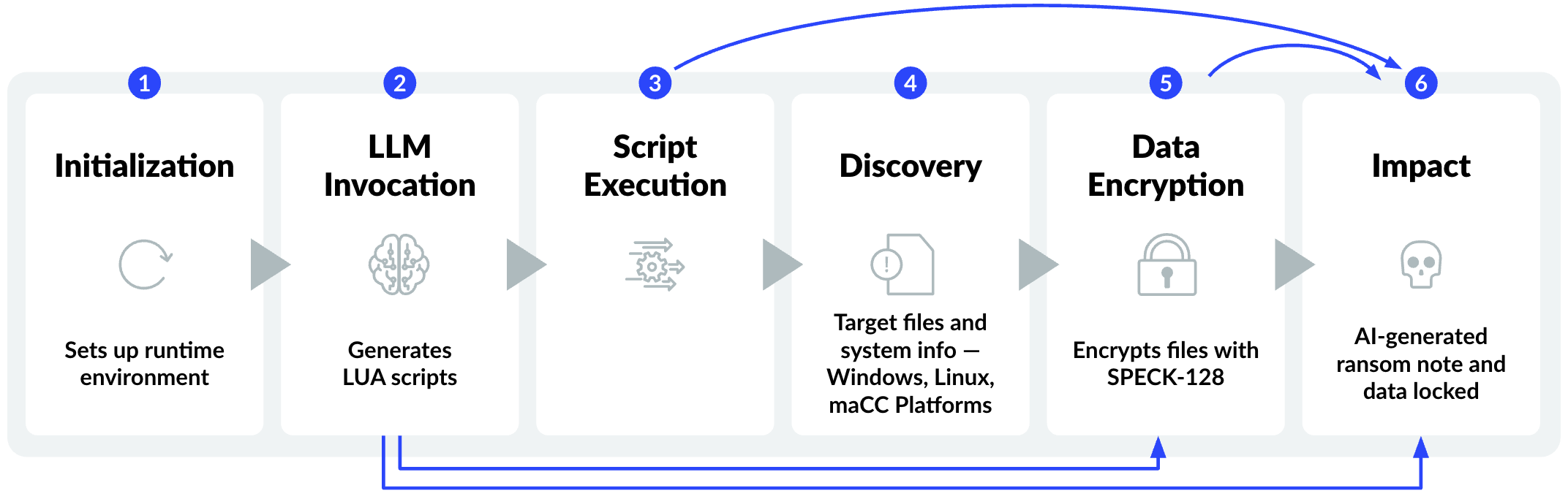
Phase 1: Autonomous Recon
- Enumerates OS, domain, privileges
- Scores targets using reasoning
- Decides stealth vs speed tradeoff
Phase 2: Self-Directed Lateral Movement
- Chooses RDP, SMB, OAuth abuse, or API tokens
- Adjusts techniques per environment
- Avoids noisy paths
Phase 3: Adaptive Persistence
- Selects persistence appropriate to host role
- Avoids redundant mechanisms
- Self-removes if risk increases
Phase 4: Intelligent Exfiltration
- Determines what data is valuable
- Chooses timing and method
- Mimics business workflows
Phase 5: Coordinated Objectives
- Ransomware only if ROI is high
- Espionage if persistence is viable
- Fraud if identity data is rich
Why Agentic Botnets Are So Dangerous
No Single Point of Failure
Taking down servers does nothing — the logic lives everywhere.
Adaptive Evasion
If detection increases, agents:
- Change tactics
- Slow down
- Go dormant
- Rewrite behavior
Human-Like Noise
Actions resemble:
- Admin activity
- DevOps workflows
- Cloud automation
- AI experimentation
This breaks signature-based and rule-based detection.
Real-World Use Cases Observed (2025–2026)
- LLM-assisted ransomware decision engines
- Autonomous phishing infrastructure
- Self-prioritizing data theft campaigns
- AI-driven supply-chain compromise
- Long-dwell espionage implants
These are not proofs of concept.
They are early-stage deployments.
Why Traditional Defenses Fail
| Control | Why It Breaks |
|---|---|
| IOC-based detection | No stable indicators |
| Network blocking | No fixed C2 |
| Sandbox analysis | Behavior adapts |
| Signature AV | Logic is dynamic |
| Static playbooks | Adversary reasons |
The CYBERDUDEBIVASH Assessment
Agentic botnets represent the most dangerous evolution of malware since polymorphism.
This is not “AI-assisted malware.”
This is malware that thinks.
Defenders are no longer fighting code —
they are fighting decision-making systems.
Defensive Strategy: How to Survive the Agentic Era
Mandatory Shifts
- Behavioral Over Signature Detection
- Detect intent, not indicators
- Identity-Centric Security
- Monitor privilege reasoning, not just access
- Continuous Threat Hunting
- Static SOC models will fail
- AI vs AI Defense
- Use defensive LLMs to detect adversarial reasoning
- Zero-Trust at Runtime
- Assume compromise, validate every action
Strategic Warning for 2026–2030
Organizations that:
- Rely on legacy SOC tools
- Treat AI as “just another app”
- Ignore identity and behavioral telemetry
Will not see agentic botnets until impact occurs.
CYBERDUDEBIVASH Closing Authority Statement
Agentic botnets mark the end of centralized command-and-control.
The battlefield has shifted from servers to cognition.
Those who do not evolve from rules – reasoning – resilience
will become training data for the next generation of attackers.
Explore CYBERDUDEBIVASH ECOSYSTEM , Apps , Services , products , Professional Training , Blogs & more Cybersecurity Services .
https://cyberdudebivash.github.io/cyberdudebivash-top-10-tools/
https://cyberdudebivash.github.io/CYBERDUDEBIVASH-PRODUCTION-APPS-SUITE/
https://cyberdudebivash.github.io/CYBERDUDEBIVASH-ECOSYSTEM
https://cyberdudebivash.github.io/CYBERDUDEBIVASH
© 2026 CyberDudeBivash Pvt. Ltd. | Global Cybersecurity Authority
Visit https://www.cyberdudebivash.com for tools, reports & services
Explore our blogs https://cyberbivash.blogspot.com https://cyberdudebivash-news.blogspot.com
& https://cryptobivash.code.blog to know more in Cybersecurity , AI & other Tech Stuffs.
#AgenticAI #Botnets #AIThreats #CyberWarfare
#LLMSecurity #MalwareEvolution #ThreatIntelligence
#ZeroTrust #CYBERDUDEBIVASH #FutureOfCybersecurity
Leave a comment