
Author: CyberDudeBivash
Powered by: CyberDudeBivash Brand | cyberdudebivash.com
Related: cyberbivash.blogspot.com
Daily Threat Intel by CyberDudeBivash
Zero-days, exploit breakdowns, IOCs, detection rules & mitigation playbooks.
Follow on LinkedIn Apps & Security Tools
CYBERDUDEBIVASH | CYBERDUDEBIVASH PVT LTD | WWW.CYBERDUDEBIVASH.COM
Why the Oracle CVSS 10 Flaw (CVE-2026-21962) Threatens Your Entire Supply Chain
Premium Vulnerability & Threat Analysis Report
By CYBERDUDEBIVASH® – Global Cybersecurity Authority
Executive Summary (Read This First)
CVE-2026-21962, a CVSS 10.0 (Critical) vulnerability affecting Oracle enterprise technology, is not just another patch-level issue.
It represents a systemic supply-chain risk capable of collapsing trust boundaries across enterprises, vendors, partners, and customers.
This vulnerability enables unauthenticated remote exploitation, potentially allowing attackers to:
- Achieve full system compromise
- Pivot across connected suppliers and service providers
- Weaponize trusted enterprise integrations as attack vectors
This is a supply-chain multiplier vulnerability, not a single-system flaw.
What Makes CVE-2026-21962 Exceptionally Dangerous
| Factor | Why It Matters |
|---|---|
| CVSS 10.0 | Maximum severity — worst-case exploitation assumed |
| Network Exploitable | No local access required |
| Unauthenticated | No credentials needed |
| Enterprise Placement | Oracle systems often sit at trust cores |
| Integration Heavy | ERP, HR, Finance, APIs, Vendors |
This combination makes the flaw catastrophic in interconnected environments.
Technical Overview (High-Level)
Vulnerability Class
- Remote Code Execution / Full Compromise
- Triggered via exposed enterprise-facing components
- Exploitable over standard business ports (HTTP/S, middleware interfaces)
Why Oracle Is a High-Value Target
Oracle systems commonly act as:
- Identity authorities
- Financial record keepers
- Supply-chain orchestration platforms
- API hubs for third-party vendors
Compromise = control over trust.
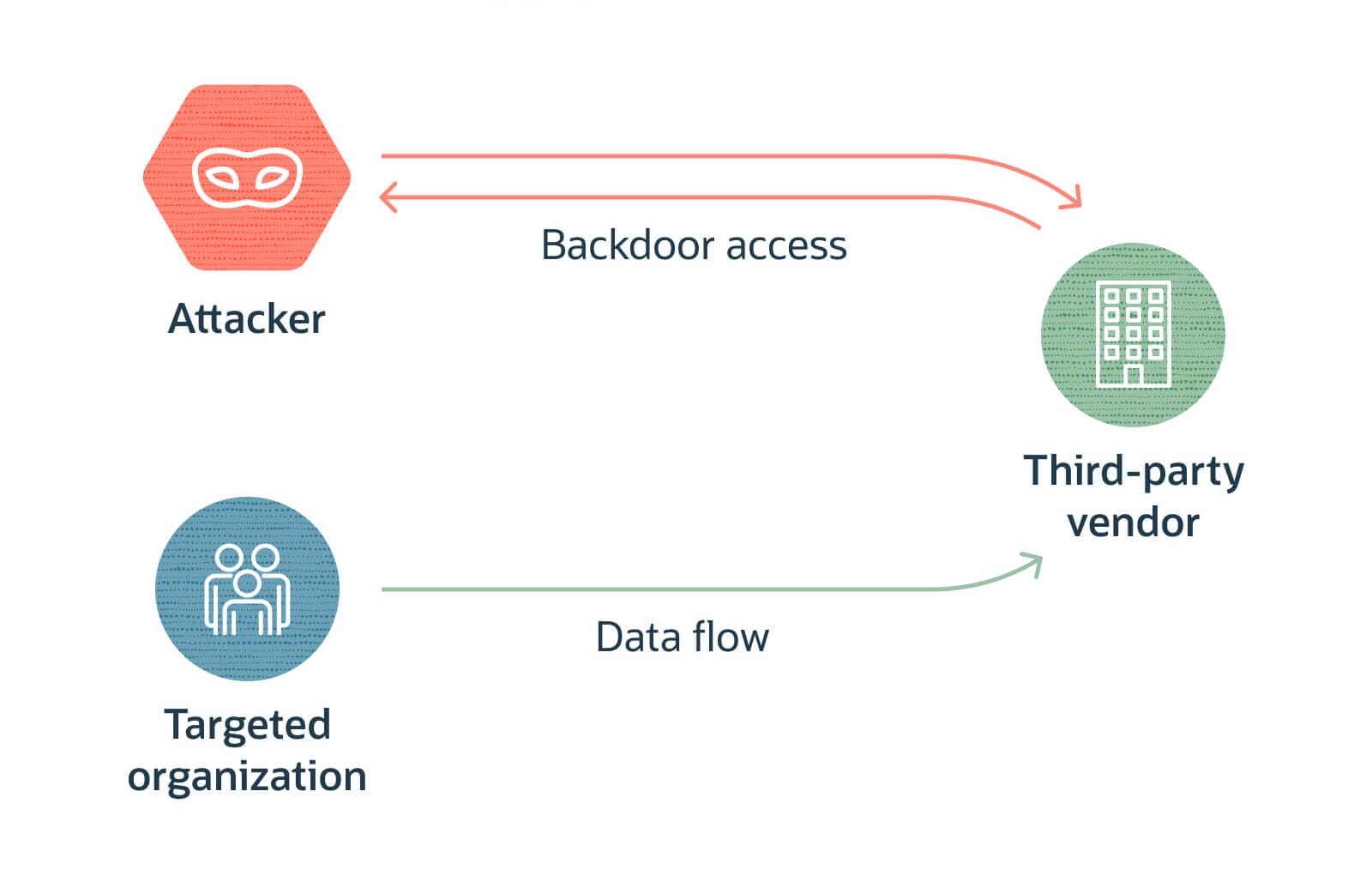
The Supply-Chain Blast Radius Explained
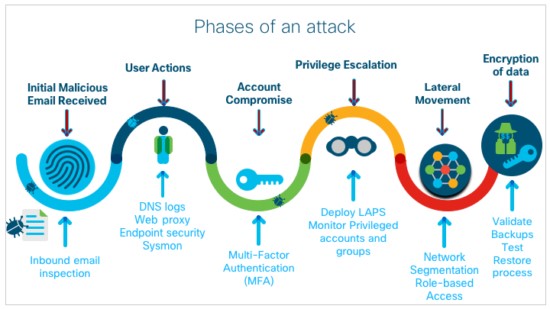
Stage 1: Initial Oracle Compromise
- Attacker exploits CVE-2026-21962
- Gains system-level access
Stage 2: Trust Abuse
- Extracts API keys, service tokens
- Hijacks SSO, LDAP, IAM integrations
- Impersonates trusted services
Stage 3: Vendor & Partner Pivot
- Malicious requests sent as “trusted traffic”
- Compromises downstream suppliers
- Injects malicious updates or data
Stage 4: Ecosystem Collapse
- Finance fraud
- Data poisoning
- Regulatory exposure
- Brand destruction
One unpatched Oracle system can silently weaponize your entire partner ecosystem.
Why Traditional Security Controls Fail Here
| Control | Why It Breaks |
|---|---|
| Firewalls | Traffic appears legitimate |
| IAM | Trust already established |
| SOC Alerts | No malware signature |
| WAF | Business logic abuse |
| AV / EDR | Exploit is server-side |
This is trust exploitation, not malware delivery.
Real-World Impact Scenarios
Financial Sector
- Fraudulent transactions
- Ledger manipulation
- Regulatory sanctions
Manufacturing & Logistics
- Supply-chain sabotage
- Production halts
- Vendor ransomware cascades
Healthcare
- Patient data exposure
- Vendor-integrated system compromise
- Life-critical service disruption
Retail & E-Commerce
- Pricing manipulation
- Payment diversion
- Customer data leaks
CYBERDUDEBIVASH Threat Assessment
Threat Level: (Extreme)
CVE-2026-21962 should be treated as an incident-level vulnerability, not a routine patch.
If exploited at scale, this flaw has SolarWinds-level consequences, but with faster propagation and less visibility.
Immediate Defensive Actions (MANDATORY)
Patch Without Delay
- Apply Oracle security updates immediately
- Verify patch success via runtime validation
Restrict External Exposure
- Remove public access where possible
- Enforce IP allowlisting
- Apply mTLS for integrations
Rotate Secrets
- API keys
- Service accounts
- OAuth tokens
- Database credentials
Monitor Trust Abuse
- Abnormal API usage
- Service-to-service anomalies
- Privilege escalations
Supply-Chain Audit
- Identify all downstream integrations
- Reassess implicit trust assumptions
Strategic Shift Required
To survive vulnerabilities like CVE-2026-21962, organizations must move from:
Perimeter Security
Zero-Trust Runtime Enforcement
Static Trust
Continuous Trust Verification
Patch-and-Pray
Threat-Informed Defense
CYBERDUDEBIVASH Closing Authority Statement
CVE-2026-21962 is not dangerous because it is exploitable.
It is dangerous because it compromises trust at scale.
In 2026, trust is the real attack surface – and Oracle sits at the center of it for thousands of enterprises.
Organizations that fail to act decisively will not just face breaches –
they will become attack conduits for everyone they do business with.
CYBERDUDEBIVASH Services & Advisory
CYBERDUDEBIVASH provides:
- Oracle Security Hardening
- Supply-Chain Risk Audits
- Zero-Trust Architecture Design
- Incident Response & Threat Hunting
- Executive & Board-Level Risk Briefings
Contact: iambivash@cyberdudebivash.com Website: https://www.cyberdudebivash.com
Leave a comment