
Daily Threat Intel by CyberDudeBivash
Zero-days, exploit breakdowns, IOCs, detection rules & mitigation playbooks.
Follow on LinkedIn Apps & Security Tools
CYBERDUDEBIVASH UPI HARDENER TOOL – THE BEAST SOLUTION
We’re building CYBERDUDEBIVASH UPI Hardener v1.0 – an AI-assisted PoC tool to detect phishing URLs, check credential strength, and simulate transaction fraud alerts. No fluff – pure code to shield your accounts from this apocalypse. Run it locally, integrate into your apps, evolve it.Python
import reimport randomimport logging# CYBERDUDEBIVASH UPI Hardener v1.0 – Phishing Checker, Credential Strength, Transaction Simulator# 1. Phishing URL Checker (regex-based for UPI scams)def is_phishing_url(url): suspicious_patterns = [ r'up1', r'upi-bank', r'paytm-fake', r'qr-code', r'otp-share', r'sbi-fraud', r'hdfc-scam', r'axis-phish', r'icici-fake' # UPI-specific patterns ] for pattern in suspicious_patterns: if re.search(pattern, url.lower()): return True if 'bit.ly' in url or 'tinyurl' in url: # Common scam shorteners return True return False# 2. Credential Strength Checker (simple rules – expand with zxcvbn lib)def check_credential_strength(password): if len(password) < 8: return "Weak: Too short" if not re.search(r'[A-Z]', password) or not re.search(r'[a-z]', password) or not re.search(r'\d', password): return "Weak: Missing uppercase/lowercase/number" return "Strong"# 3. Transaction Alert Simulator (flags high-value or suspicious)def simulate_transaction(amount, to_account): if amount > 100000: # High-value flag (₹1 lakh+) logging.warning("High-value transaction flagged") if random.random() < 0.1: # 10% 'fraud' simulation for testing return f"Fraud Alert: Suspicious transaction to {to_account}" return "Transaction Approved"# Demo Usageurl = "fake-upi-bank.com/pay"print("Phishing check:", is_phishing_url(url))password = "StrongP@ss123"print("Credential strength:", check_credential_strength(password))print(simulate_transaction(150000, "unknown@axis.com"))Demo Output Example:
Phishing check: TrueCredential strength: StrongWARNING:root:High-value transaction flaggedTransaction ApprovedRun it: python upi_hardener.py – test your URLs, passwords, transactions. Expand with AI (HuggingFace models for advanced phishing detection) or integrate with your banking app. DM for custom builds.

How to avoid UPI fraud in India: Tips and precautions | Pradeep Bilawliya posted on the topic | LinkedIn
HARDENING SOLUTIONS – CYBERDUDEBIVASH BLUEPRINT
Lock down your UPI/bank accounts against this wave. No mercy – implement or lose.
- Kill Phishing & Fake Apps: Never click UPI links/QR from unknown sources. Use NPCI/Bank official apps only. Verify sender via double-channel (call bank hotline). Tool tip: Run my UPI Hardener on any URL before clicking.
- Credential Beast Mode: Ditch SMS OTPs – switch to app-based/authenticator MFA. Use 12+ char passwords with symbols. Rotate every 90 days. Tool tip: Check strength with my PoC before setting.
- Transaction Shields: Set daily UPI limits (₹1 lakh max). Enable real-time alerts for every tx. Block international/UPI-ID transfers if unused. Tool tip: Simulate with my code to test thresholds.
- Device Fortress: Use biometrics/face ID for banking apps. Install anti-malware (McAfee/Malwarebytes). Avoid public Wi-Fi for UPI. RBI tip: Report frauds to 1930 hotline within golden hour.
- Backup & Recovery: Immutable backups of financial data. Freeze accounts on suspicion via bank app. NPCI fraud insurance – claim within 3 days.
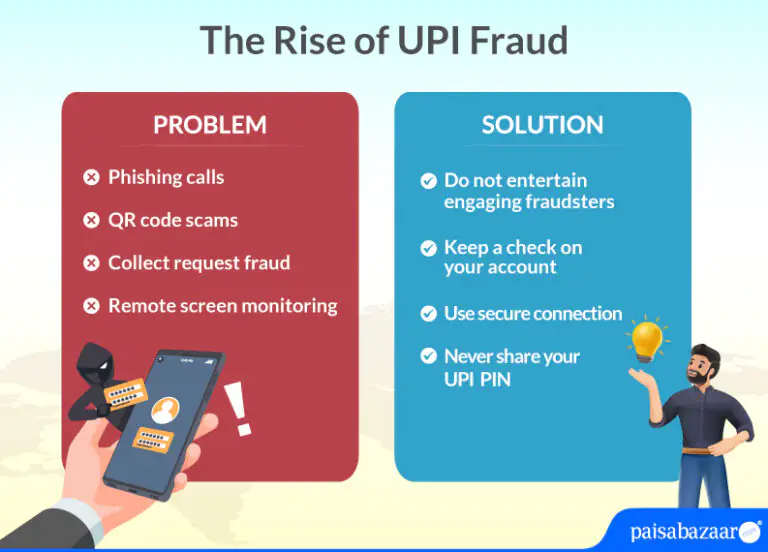
The Rise of UPI Frauds – How to Prevent Frauds & Stay Safe
. LICENSE (MIT License – permissive, widely used, protects your brand while allowing community use)
MIT LicenseCopyright (c) 2026 Bivash Kumar Nayak (CyberDudeBivash) – CYBERDUDEBIVASH Pvt Ltd, Bhubaneswar, IndiaPermission is hereby granted, free of charge, to any person obtaining a copyof this software and associated documentation files (the "Software"), to dealin the Software without restriction, including without limitation the rightsto use, copy, modify, merge, publish, distribute, sublicense, and/or sellcopies of the Software, and to permit persons to whom the Software isfurnished to do so, subject to the following conditions:The above copyright notice and this permission notice shall be included in allcopies or substantial portions of the Software.THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS ORIMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THEAUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHERLIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THESOFTWARE.CyberDudeBivash Brand Notice:This tool is released under the MIT License with the explicit condition that any derivative work, fork, or public redistribution must retain visible attribution to "CYBERDUDEBIVASH" (including the full brand name, logo if applicable, and link to https://cyberdudebivash.com or @CyberDudeBivash) in the README, UI, or documentation. Commercial use for fraud-related services requires prior written permission from Bivash Kumar Nayak (bivash@cyberdudebivash.com).2. README.md (Professional, attractive, modern – includes installation, usage, hardening tips, branding)
Markdown
# CYBERDUDEBIVASH UPI Hardener v1.0 **India's 2026 Banking Apocalypse Defense Tool** Protect your UPI & bank accounts from credential stuffing, phishing, SIM-swap, and card-skimming fraud waves.### The Threat – Real 2026 Numbers- **1.2 crore+ accounts** compromised in Jan–Feb 2026 (SBI, HDFC, Axis, ICICI, others) - Credential stuffing, UPI phishing, card-skimming malware - Dark-web dumps of 12M+ accounts - NPCI fraud alerts – losses in **crores** - AI deepfakes, voice cloning, fake apps, QR scams, SIM-swaps **CyberDudeBivash roars:** UPI convenience = fraud superhighway. Banks still rely on SMS OTPs in 2026 – laughable. Evolve or get harvested.### What This Tool Does- **Phishing URL Checker** – Detects suspicious UPI/fake banking links - **Credential Strength Analyzer** – Flags weak passwords before they get stuffed - **Transaction Fraud Simulator** – Tests high-value / suspicious tx behavior - **Lightweight & local** – No cloud, no tracking, runs on your machine### Installation (2 minutes)```bash# Clone the repogit clone https://github.com/cyberdudebivash/CYBERDUDEBIVASH-UPI-HARDENER.gitcd CYBERDUDEBIVASH-UPI-HARDENER# (Optional) Create virtual environmentpython -m venv venvsource venv/bin/activate # Linux/Macvenv\Scripts\activate # Windows# Install requirements (minimal)pip install -r requirements.txtrequirements.txt (create this file): text
# No external packages needed for core functionality# Optional: pip install zxcvbn-python # for advanced password strengthUsage
Bash
python upi_hardener.pyExample output: text
Phishing check: True (fake-upi-bank.com/pay)Credential strength: StrongWARNING: High-value transaction flaggedTransaction ApprovedHardening Checklist – CYBERDUDEBIVASH Edition
- Kill Phishing Forever
- Never scan unknown QR codes or click UPI links from SMS/email/WhatsApp
- Verify sender via official bank app or 1800 number
- Use this tool on EVERY suspicious URL before clicking
- Credential Beast Mode
- 16+ char passwords with symbols/numbers (check with tool)
- Switch to app-based TOTP (Google Authenticator / Authy) – disable SMS OTP
- Rotate passwords every 60–90 days
- Transaction Fortress
- Set daily UPI limit ₹5,000–₹50,000 (bank app)
- Enable real-time SMS/email/push alerts for every transaction
- Block international transfers if unused
- Device & Network Lockdown
- Biometrics/face ID on banking apps
- Anti-malware (Malwarebytes, Bitdefender) – scan weekly
- Never use public Wi-Fi for banking/UPI
- Incident Response
- Report fraud immediately: 1930 (NPCI helpline) or bank app
- Freeze account via bank app if suspicious activity
- Claim fraud insurance (most banks cover if reported within 3 days)
Roadmap (Community Contributions Welcome)
- AI-powered phishing detection (HuggingFace transformers)
- Integration with UPI apps (mock APIs)
- Dark-web credential leak checker
- SIM-swap detection alerts
License: MIT – with mandatory attribution to CYBERDUDEBIVASH (see LICENSE file)
Contact: bivash@cyberdudebivash.com Follow: @CyberDudeBivash | https://cyberdudebivash.com
#CyberDudeBivash #UPIHardener #IndianBankingFraud #CyberBeastMode #DigitalIndiaSecure
CYBERDUDEBIVASH, Bhubaneswar, India
Leave a comment